A massive distributed brute force attack campaign targeting WordPress sites started this morning at 3am Universal Time, 7pm Pacific Time. The attack is broad in that it uses a large number of attacking IPs, and is also deep in that each IP is generating a huge number of attacks. This is the most aggressive campaign we have seen to date, peaking at over 14 million attacks per hour.
The campaign continues to ramp up in volume during the past hour as we publish this post. A graph of the attack volumes is shown below which shows the number of attacks per hour and the number of attacking IPs that we see each hour.
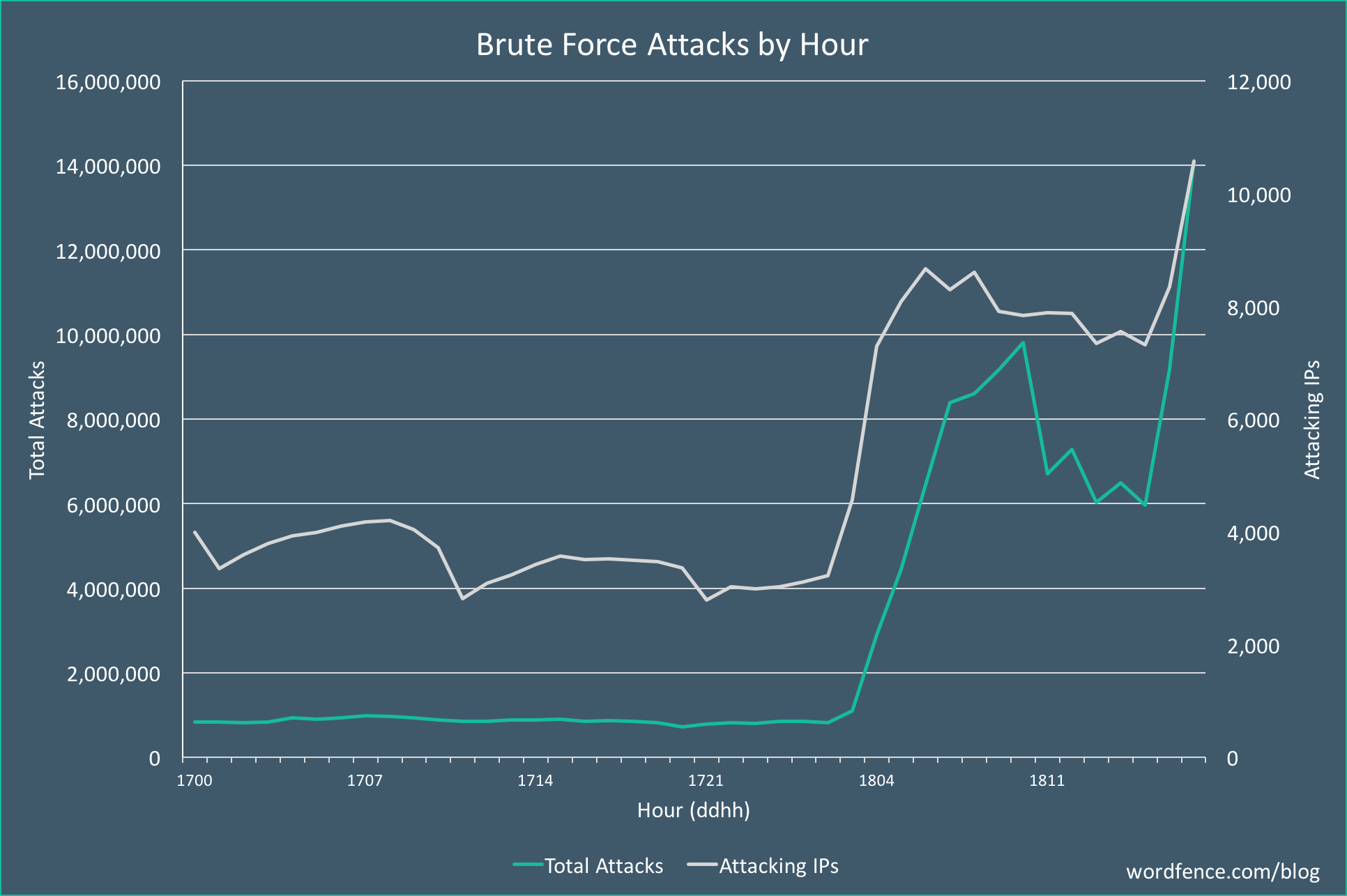
This all happened unattended early Tuesday morning. We continue to monitor the attack and are analyzing its origin and who is behind it.
What we know at this time:
1. The attack has so far peaked at 14.1 million attacks per hour.
2. The total number of IPs involved at this time is over 10,000.
3. We are seeing up to 190,000 WordPress sites targeted per hour.
4. This is the most aggressive attack we have ever seen by hourly attack volume.
A possible explanation for this new massive increase in brute force attacks
On December 5th, a massive database of hacked credentials emerged. It contains over 1.4 billion username/password pairs. Approximately 14% of the database contains credentials that have not been seen before. The database is also searchable and easy to use.
Historically, brute force attacks targeting WordPress have not been very successful. This new database provides fresh credentials that, when matched with a WordPress username, may provide a higher success rate for attackers targeting sites that do not have any protection.
Protect yourself:
We deeply recommend installation and activation of the following WordPress plugins:
1. Rename WP login plugin for renaming the login url to your website dashboard.
2. Disable XML-RPC protocol plugin
3. Wordfence plugin
4. Additionally, and/or optional, you can install and activate JSON API plugin.
Of course, change of your default WordPress username (admin) and password is highly recommended.



